Azure Active Directory Integration
Learn how to integrate Azure Active Directory with the super.AI platform.
Overview
super.AI supports Azure Active Directory SSO integration on request as an Azure Active Directory (AD) Enterprise Application. This means customer organization users can sign up in our platform using their Active Directory (AD) credentials and be automatically added to a super.AI Organization resource mapping the customer organization.
How to integrate with super.AI Organizations
In the following paragraph we describe the required steps to integrate with super.AI’s Organisations feature leveraging Azure Active Directory.
-
The customer must request super.AI access to this feature via their Azure AD Administrator
-
Subsequently, super.AI will provide the Identifier (Entity ID) and Reply URL required for the customer to create an Enterprise Application in his AD.
-
Once the Enterprise Application is created by the Azure AD Administrator, the customer must provide super.AI with the generated App Federation Metadata Url and the claim names of email (e.g “http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress”) and groups (”http://schemas.microsoft.com/ws/2008/06/identity/claims/groups”). Refer to the step by step guide on how to setup the enterprise application below.
-
AD Group object id which grants the super.AI organization Owner role to its members. See the section below on how to manage AD user access to super.AI.
-
Once onboarded, super.AI will provide the customer a custom URL to sign up/sign in using Azure Active directory.
-
Once users have signed up for super.AI using their Azure credentials they can use SSO
Step by step to add super.AI customer pool as an enterprise application in Azure Active Directory
To add new application in Azure Active Directory:
- Log in to the Azure Portal.
- In the Azure Services section, choose Azure Active Directory.
- In the left sidebar, choose Enterprise applications.
- Choose New application.
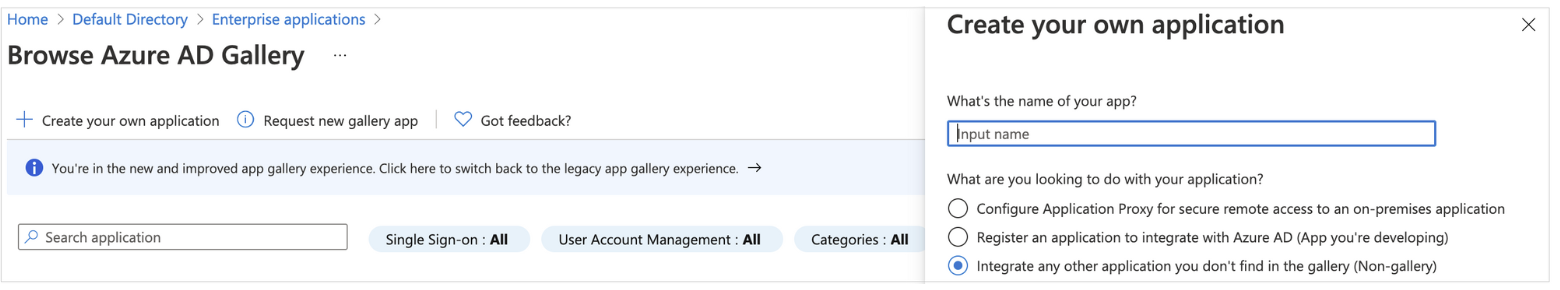
- On the Browse Azure AD Gallery page, choose Create your own application.
- Under What’s the name of your app?, enter a name for your application and select Integrate any other application you don’t find in the gallery (Non-gallery), as shown in next figure. Choose Create.
To set up Single Sign-on using SAML
-
On the Getting started page, in the Set up single sign on tile, choose Get started, as shown in next figure.

-
On the next screen, select SAML.
-
In the middle pane under Set up Single Sign-On with SAML, in the Basic SAML Configuration section, choose the edit icon.

-
In the right pane under Basic SAML Configuration, replace the default Identifier ID (Entity ID) with the Identifier (Entity ID) you received previously. In the Reply URL (Assertion Consumer Service URL) field, enter the Reply URL you received previously, as shown in the previous figure. Choose Save.
-
In the middle pane under Set up Single Sign-On with SAML, in the User Attributes & Claims section, choose Edit.
-
Choose Add a group claim.
-
On the User Attributes & Claims page, in the right pane under Group Claims, select Groups assigned to the application, leave Source attribute as Group ID, as shown in the next figure. Choose Save.

This adds the group claim so that super.AI customer pool can receive the group membership detail of the authenticated user as part of the SAML assertion.
-
In a text editor, note down the Claim names for email and groups under Additional claims, as shown in the previous figure. You’ll need to inform of those to super.AI
-
Close the User Attributes & Claims screen by choosing the X in the top right corner. You’ll be redirected to the Set up Single Sign-on with SAML page.
-
Scroll down to the SAML Signing Certificate section, and copy the App Federation Metadata Url by choosing the copy into clipboard icon (highlighted with red arrow in the last figure). You’ll need to inform of this to super.AI

How to manage AD Users access to super.AI
Super.AI has two main roles at the organization level Owner and Member. Owners are able to see and manage all projects in the entire organization and Members can only see projects for which they are specifically invited to.
Any Azure AD User that is directly assigned to the AD Enterprise Application or that is part of a group assigned to the AD Enterprise Application will be able to access super.AI as a Member. In order to grant Owner privileges to any AD User, the Enterprise Application Admin needs to add that AD User to the group shared with super.AI during the AD setup.
If a user belongs to the Azure AD Owner Group, then modifying the role within super.AI members view will have no effect, since the Azure AD is always prioritized.
Updated 5 months ago
